Do you use a monitoring program to watch your Windows Event logs? If you do, and you’re a Zerto user you will love the script I just finished up!
Zerto has the ability to send email alerts as well as trigger vCenter alarms when something is wrong (You can also see the alerts in the Zerto Analytics portal too). For many people, this is all they need, but for larger environments, a consolidated monitoring platform is often used. Zerto currently does not integrate into any 3rd party monitoring tool natively. So using a tool like SCOM, SolarWinds, Nagios, etc, is not an option… but it can be with this script!
Pushing Zerto Alerts to the Windows App Event Log
All of the alert information in the Zerto dashboard can be obtained through the Zerto REST API, and once you have them you can do anything you want. Like, push them into the Windows Application Event Log using a PowerShell script. Here is what it looks like when the script is doing its job:
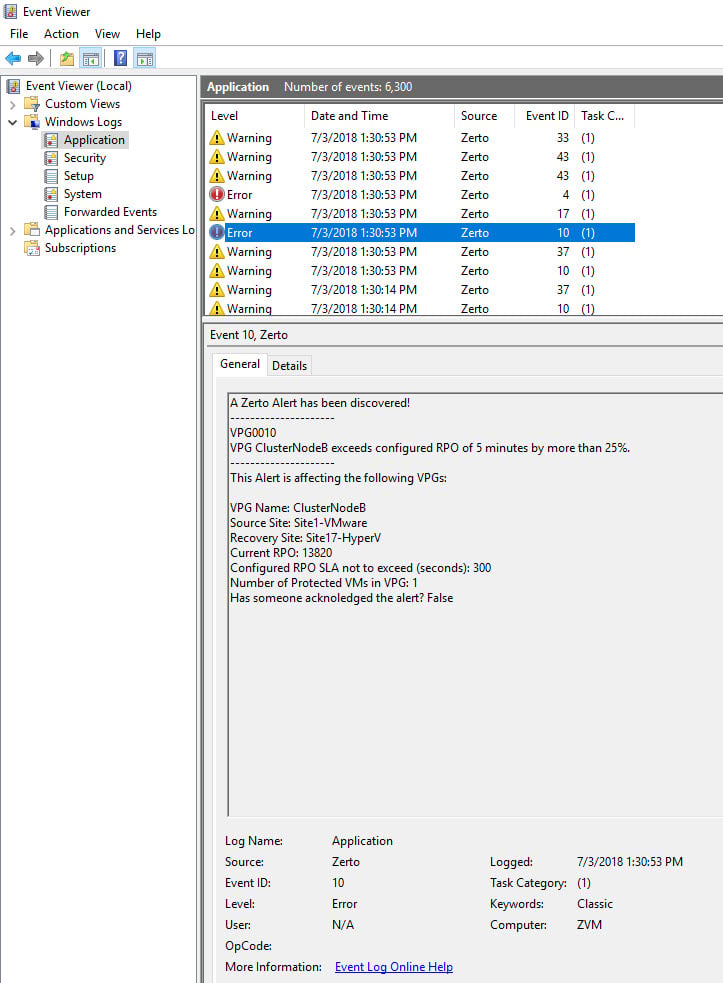
Currently, the script only pushes Warning and Error alerts to the event log, but you can modify it to fit your needs.
Script Installation
To get the script head over to Github. The repository for this script is https://github.com/recklessop/ZertoScripts
You will need two PowerShell scripts from this repo, they are:
- ZVMAlertToEventLog.ps1
- passEncrypt.ps1
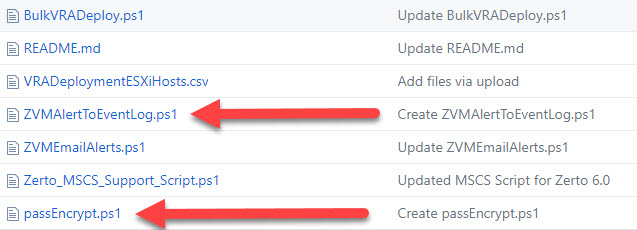
The script that gets scheduled as a Windows task is the ZVMAlertToEventLog.ps1 script, the passEncrypt.ps1 script simply encrypts your Zerto password so that it is not stored in clear text on the ZVM.
Prerequisite – Before this script will work you need to create a “Zerto” Application log source. This is super easy to do and only needs to be done one time.
Open Powershell and type the following:
New-EventLog -Source “Zerto” -LogName “Application”
Step 1 – Encrypt Your password
In the few scripts I have written for customers, I always get dinged on storing the password for something in clear text. So before we go any further we will run the passEncrypt.ps1 script and enter your password so it encrypts it. Note! You MUST run this script on the machine where the alert script will run.
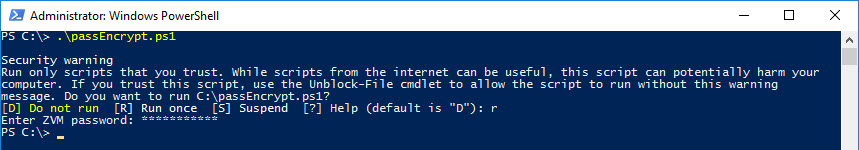
Once you have run the script there will be a text file called “passwd.txt” on the root of your C:\ drive. Open it and copy its content.
We will now paste the encrypted password string into the ZVMAlertToEventLog.ps1 script.
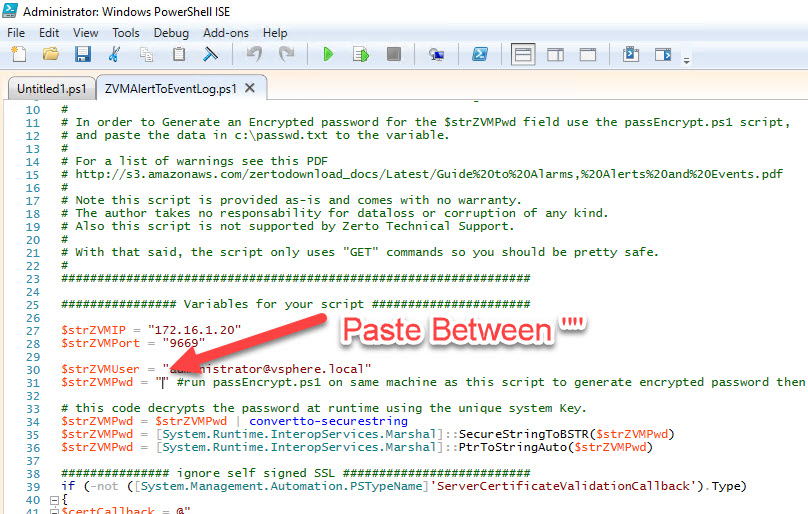
While you are in the ZVMAlertToEventLog.ps1 script make sure to change the ZVM IP address and username to whatever values are required for your environment.
Save the script.
Step 2 – Test Run the script
While in Powershell ISE you can run the script to see that everything works OK. You should simply see the script run, then return you to a PowerShell prompt.
Next check the Windows Application Event log to see if anything was inserted. Keep In mind if you do not have any alerts nothing gets inserted. So if you want to cause an alert, just pause a VPG for a while.
Step 3 – Schedule the Script in Windows Scheduled Tasks
Before we schedule the script, make sure to open up a PowerShell prompt as administrator and change the Execution policy to Unrestricted, since this script is unsigned.
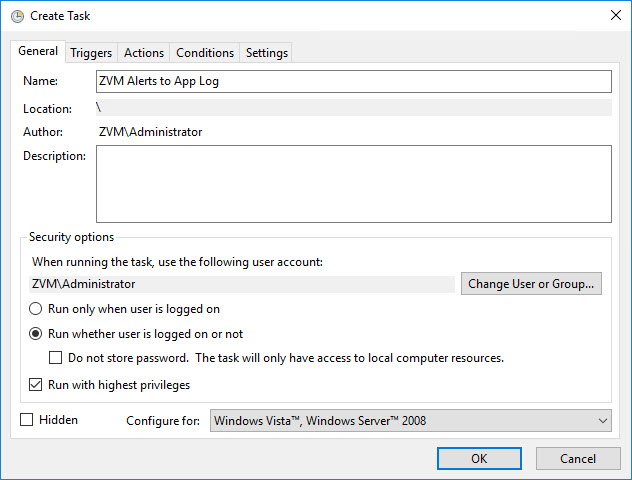
Once you have verified that it runs properly, go into Task Scheduler and create a new task. (Not a Basic Task). Give it a Name, then select Run whether user is logged on or not, and also select Run with Highest Priveledges.
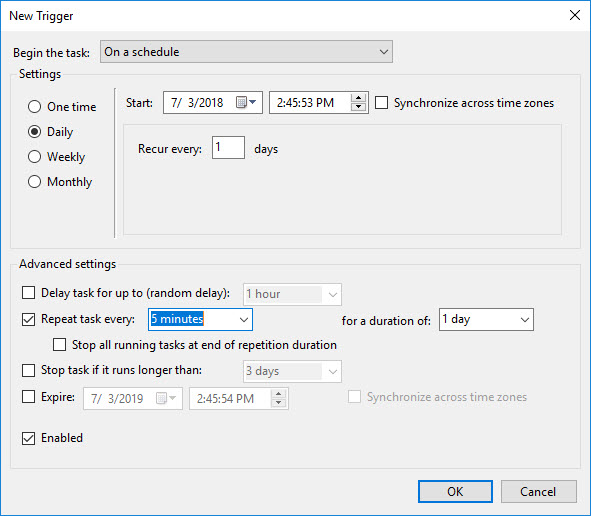
Next, on the Triggers tab click New then configure a “Daily” schedule which also repeats the task every few minutes. I would say anything under an hour would be fine. But it’s totally up to you.
On the Actions tab, click New then type powershell.exe in the Program box and in the argument box add -file “C:\ZVMAlertToEventLog.ps1”, or whatever the path to the script is.
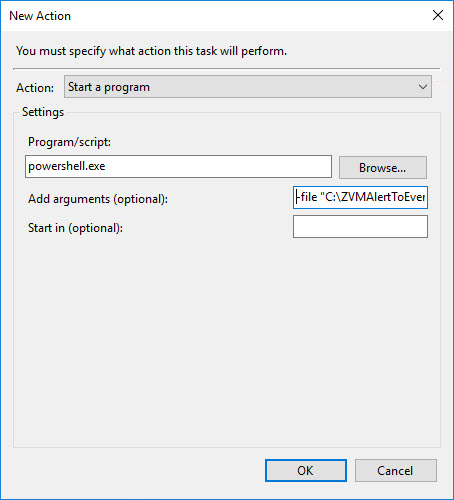
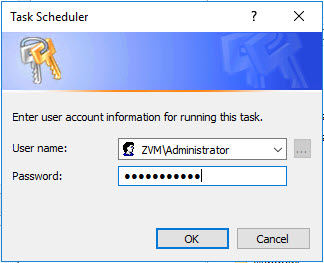
Click OK on the Actions box, as well as the New Task box as well. Then you will be asked for the credentials you want to run the script as.
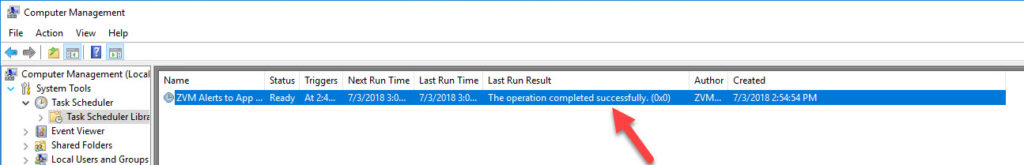
You should now see your scheduled task in the list and be able to see what the last exist status was after it runs for the first time.
Conclusion
You can now have your 3rd party monitoring platform check the Windows Application logs for Zerto alerts. Some things to keep in mind are that the event source will always be “Zerto” and the Event ID will be the Zerto Alert ID (minus the string portion)… So for example, if you have a VRA problem the alert in the Zerto GUI may be VRA0033, in the Windows App Event log it will just be 33. I couldn’t pass a string so I removed the text and just pass the numeric value.
You can also always scrape the Message body for more details too.
If this works for you, please post a comment and shoot us a screenshot or something of it working. Thanks, everyone!
![]()




2016 Windows host will need to add Event viewer source “Zerto” first.
New-EventLog –LogName Application –Source “Zerto”
Thank for the info Paul. I may have created that a while ago and forgot the add the step to my documentation!
Paul
When I run the script it shows the message below
Write-EventLog : Cannot validate argument on parameter ‘Message’. The argument is null or empty. Provide an argument that is not null or
empty, and then try the command again.
At C:\Temp\ScriptZerto\ZVMAlertToEventLog.ps1:135 char:110
+ … rce “Zerto” -EventID $zID -EntryType $alert.Level -Message $EventBody
+ ~~~~~~~~~~
+ CategoryInfo : InvalidData: (:) [Write-EventLog], ParameterBindingValidationException
+ FullyQualifiedErrorId : ParameterArgumentValidationError,Microsoft.PowerShell.Commands.WriteEventLogCommand
I’d bet something else in the script isn’t working. As it is saying that the event message variable is empty. So the script isn’t properly getting data into that variable.
I am running on Windows 2016 server for my ZVM. When I first ran the script, I was getting the following error:
Invoke-WebRequest : The request was aborted: Could not create SSL/TLS secure channel.
At C:\Users\usc-s2va\Documents\ZVMAlertToEventLog.ps1:85 char:30
+ … nResponse = Invoke-WebRequest -Uri $xZertoSessionURL -Headers $header …
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidOperation: (System.Net.HttpWebRequest:HttpWebRequest) [Invoke-WebRequest], WebException
+ FullyQualifiedErrorId : WebCmdletWebResponseException,Microsoft.PowerShell.Commands.InvokeWebRequestCommand
The fix is to insert the following above the “ignore self signed SSL” comment on or around line 40:
[Net.ServicePointManager]::SecurityProtocol = “tls12, tls11, tls”
It is working like a champ! Thanks.
Thanks for the info Daryl!