Amanda Katona, Cloud Native Community Engagement Director, VMware
With KubeCon + CloudNativeCon North America 2019 closing out the calendar year, it’s a great opportunity to reflect on the success of Kubernetes and its ecosystem. There’s such positive momentum we can carry into the new year for renewed energy, focus, and community spirit.
In August, we announced the launch of VMware Tanzu—a portfolio of solutions to transform the way organizations build, run, and manage applications on Kubernetes. VMware Tanzu solutions are built on key cloud native open source projects—they can be found in our VMware Tanzu GitHub organization at github.com/vmware-tanzu.
These projects continue to grow and thrive. Below, you can find a quick recap of the recent progress in each project. Come find project maintainers or take a mini-lab at KubeCon—we’ll be at the VMware booth (D6).
Top project highlights include:
- Contour, the scalable multi-team Kubernetes ingress controller for Envoy, shipped version 1.0. We are now signaling to the community that we are committed to a stable, backward-compatible version of Contour and its CRDs.
- Velero, used for Kubernetes cluster back-up and data migration, continues to introduce key features based on community requests with version 1.2, enabling users to manage their Kubernetes data and enable business continuity in disaster recovery situations.
- Sonobuoy started as a diagnostic tool to help users understand the state of a Kubernetes cluster by running a choice of configuration tests. Today, its flexible design and implementation of a Sonobuoy plugincan spot security concerns in your clusters by using the CIS benchmarks.
- Octant continues to add new features to help developers visually demystify their applications in a Kubernetes cluster. Its pluggable architecture paves the road for future integrations that add context-related content to the applications views.
- A new open source tool, Crash Recovery and Diagnostics for Kubernetes, was released. It is designed to help troubleshoot problem clusters by automating the collection of machine states and diagnostic data from unstable or inoperable clusters for support teams to analyze.
Let’s dive into the updates:
Contour 1.0
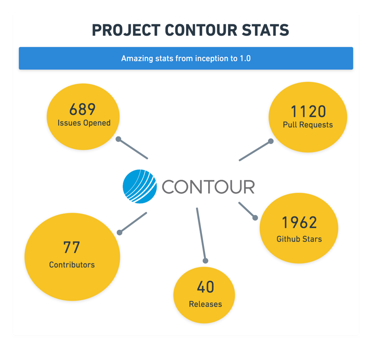
We launched Contour just two years ago, so reaching the recent version 1.0 milestone is a great achievement. Contour is a high performance, multi-team Ingress controller for Kubernetes that works by deploying the Envoy proxy as a reverse proxy and load balancer.
Contour 1.0 moved the HTTPProxy CRD to version 1 and represents our commitment to evolve that API in a backward-compatible manner. Users of `IngressRoute` should plan to migrate to the new `HTTPProxy` as well as look to utilize the secure, split deployment model with leadership election. Find out more at projectcontour.io/announcing-contour-1.0/
Contour maintainers will be at KubeCon + CloudNativeCon North America 2019 and would love to chat with you. Join the Contour community lunch on Tuesday, November 19, at 12:30 PM in the San Diego Convention Center. Come to VMware booth D6 or look for the Contour signs in the lunch area to find the team. There will also be mini-labs at the booth to get hands-on with the project.
Velero 1.2
Velero is an open source tool to safely back up and restore, perform disaster recovery, and migrate Kubernetes cluster resources and persistent volumes. Velero continues to evolve with the release of version 1.2.
With version 1.2, we’ve extracted the AWS, Azure, and GCP plugins into their own repositories, one per provider. This change reduces the size of the core Velero binary, and opens the door for the plugins to be maintained and released independently of core Velero.
In addition, we’ve made some Restic Integration Improvements. Restic backup and restore progress is now captured during execution, providing a new level of visibility into restic operations. Restic backups of persistent volume claims (PVCs) now remain incremental across pod reschedules, potentially making such backups faster. Read-write-many volumes are now backed up just once per Velero backup, which speeds up backups and prevents potential restore issues due to multiple copies of the backup being processed simultaneously.
To help you secure your important backup data, we’ve added support for more forms of server-side encryption of backup data on AWS and GCP. On AWS, Velero now supports Amazon S3-managed encryption keys (SSE-S3), which uses AES256 encryption. On GCP, Velero now supports using a specific Cloud KMS key for server-side encryption. Read more at velero.io/blog/velero-1.2-sets-sail.
Meet the Velero maintainers at KubeCon + CloudNativeCon at the Velero community lunch on Wednesday, November 20, at 12:30 PM in the conference’s lunch area—look for the Velero signs. Make sure to stop by the VMware booth (D6) to experiment with Velero in a hands-on mini-lab.
Sonobuoy CIS Benchmark
Sonobuoy is a diagnostic tool that makes it easier to understand the state of a Kubernetes cluster by running a choice of configuration tests in an accessible and non-destructive manner. Sonobuoy was always designed to facilitate third-party plugins to accommodate custom testing requirements, but until recently, it made some advanced plugins impossible to create.
One often-requested plugin that had been difficult to implement was a plugin based on the CIS benchmarks. The Center for Internet Security (CIS) publishes a set of prescriptive security benchmarks for establishing a secure configuration posture for Kubernetes.
Now, we’ve taken these benchmarks and implemented them as a Sonobuoy plugin so that you can spot security concerns in your own clusters. Learn how to run the CIS benchmark over at sonobuoy.io/cis-benchmark-plugin.
Learn about the Cloud Native Computing Foundation’s vendor certification program and how Sonobuoy is the underlying technology to support the program. And just like Velero and Contour, you’ll find project maintainers at KubeCon—stop by the VMware booth for more information.
Crash Recovery and Diagnostics for Kubernetes
Crash Diagnostics is designed to help troubleshoot problem clusters by automating the collection of machine states and diagnostic data from unstable or inoperable clusters for a cluster operation or support team to analyze.To specify the machine resources to collect from the cluster, Crash Diagnostics uses a series of commands that are declared in a file called a diagnostic file. Like a Dockerfile, the diagnostics file is a collection of line-by-line directives with commands that are executed on each specified cluster machine. The output of each command from each machine is then added to a tar file that can be sent to support teams for further analysis.
Check out the project on GitHub at github.com/vmware-tanzu/crash-diagnostics.
Octant
In a perfect world, you would deploy applications to clusters and nothing else would be a problem. In the Kubernetes world, it isn’t that simple yet. Because Kubernetes workloads are composed of multiple objects, even simple actions can be complex. This complexity is why we created Octant, an open source developer-centric web interface for Kubernetes that lets you inspect a Kubernetes cluster and its applications.
Octant supports CRDs and has recently replaced event streams with websockets, opening up possibilities of future plugins. As the Octant project continues to evolve, the goal remains to make Kubernetes more accessible, and for Octant to become a part of the standard toolkit for working with clusters.
One improvement to Octant is a new applications view available behind a feature flag. Another improvement is that environment variables and flags are now interchangeable to simplify usage when proxying Octant. In addition, we removed the need to manually compile for ARM to make it easier for users to get started as quickly as possible.
Octant is available as a standalone binary, and also easily installable using Homebrew, Chocolatey, and Scoop. Nightly releases can also be downloaded to give you faster access to the latest features.
Catch KubeCon co-chair Bryan Liles during TGI
Kubernetes held in the VMware
Community Lounge on Wednesday at 1 PM to talk more about Octant. To experience
Octant for yourself, stop by the VMware booth for a quick mini-lab. To read
more about Octant and join the community, head over to octant.dev.
![]()




Pingback: All the news you missed at KubeCon 2019 | Justin's IT Blog