How annoying it is…
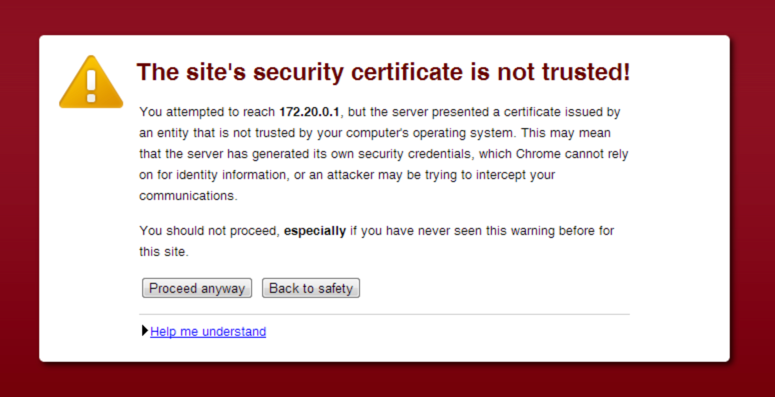
How many servers, or hardware management interfaces, or other devices on your network make you do those extra clicks to get to them? You know, the ones where you agree that you have intelligence and you want to proceed even though the browser says you shouldn’t?
After you read this article you should be able to take Zerto Virtual Replication off the list, as we are going to walk through my way for swapping out the self-signed SSL certificate with a signed SSL cert from your Active Directory Domain Certificate Authority. The biggest difference between this how-to and the official Zerto method is that I’m going to use a GUI utility on the ZVM instead of installing OpenSSL and having you create the CSR from the command line. This will make it easier for people who have not worked with the OpenSSL CLI utility.
Prerequisites
- Active Directory Domain
- Microsoft Certificate Services
- DigiCert Certificate Utility for Windows (get it here https://www.digicert.com/util/)
I won’t cover how to set up Active Directory Certificate Services in this article as there are plenty of great posts out there, it’s also a pretty easy process. So, where we will start is by downloading the DigiCert Utility to our ZVM machine.
Generating a Certificate Signing Request
In the official Zerto KB article, the OpenSSL CLI is used to generate a certificate request on the Zerto server but some people find it confusing. In my version, we are going to use an awesome app by DigiCert that is all GUI based.
Get the DigiCert Utility
The first thing we need to do (from our Zerto Virtual Manager) is to download the DigiCert Certificate Utility from https://digicert.com/util/
Next, move it over to the desktop, or somewhere you can access. (The utility doesn’t do an installation, which is why I recommend the desktop.)
Now run the DigiCertUtil.exe program that you just moved, accept the license agreement, then you should see the SSL tab of the utility. This is where we want to be so we can run the “Create CSR” wizard at the top right.
Now we can enter the same information that you would have entered in the OpenSSL CLI if you were using that method.
[stextbox id=’info’]If you do not know your “Common Name”, check Windows Server Manager for the FQDN of your ZVM. For example, I will use S2-ZVM.labrack.xyz for my server.[/stextbox]
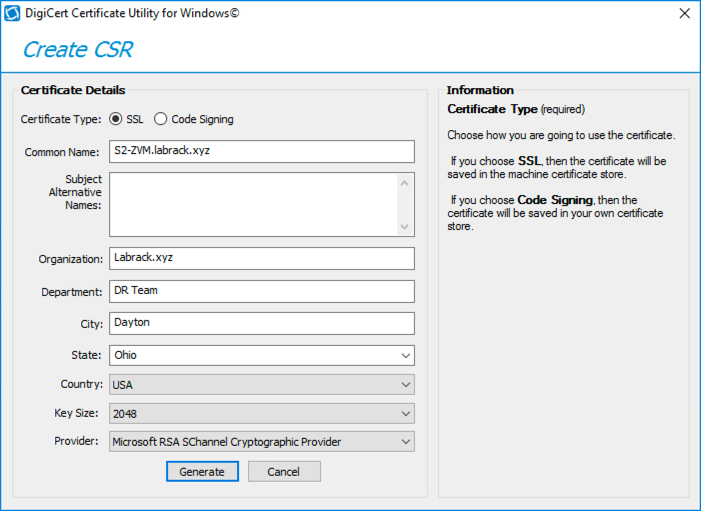
Once you have entered all of your information click “Generate” at the bottom. You should get a popup box that shows your new CSR. You need to copy the CSR or save it to a file, I recommend both!
The next step is to get our certificate request signed.
Signing a CSR with Microsoft AD Certificate Services
There are many ways to get your SSL certificate signed. If we were creating a cert for an internet facing web server we might want to use DigiCert (the place we got the Windows Utility from), but for an internal server like Zerto Manager, we will most likely want to sign the certificate with something like Microsoft AD Certificate Services.
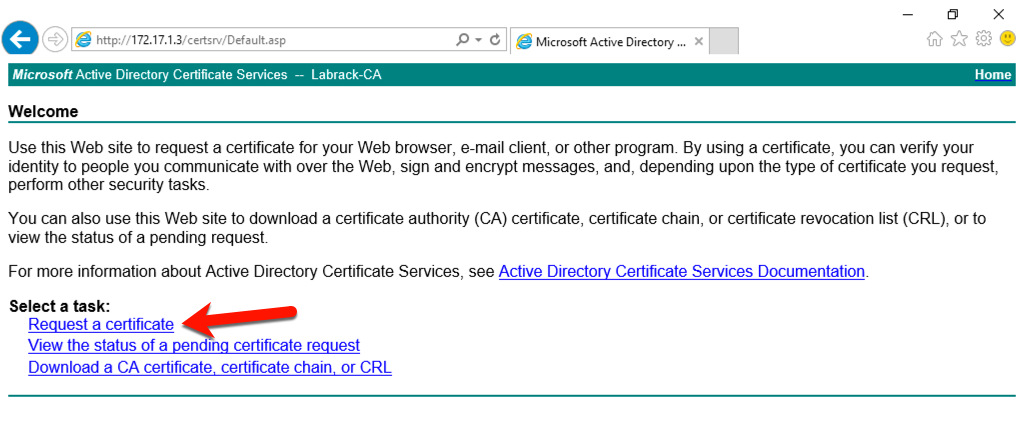
Chances are your domain already has a certificate services server somewhere, if not just search google for a how-to on setting one up, they don’t take too long to do. Then once you are done you can navigate to the web request portal that lives on your ADCS server. You will see a list of available options, and we need to pick the “Request a certificate” link.
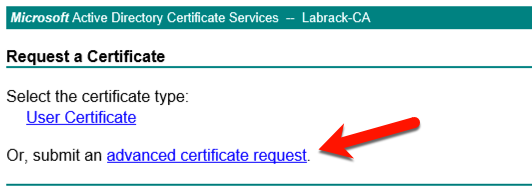
On the next screen select “advanced certificate request” link.
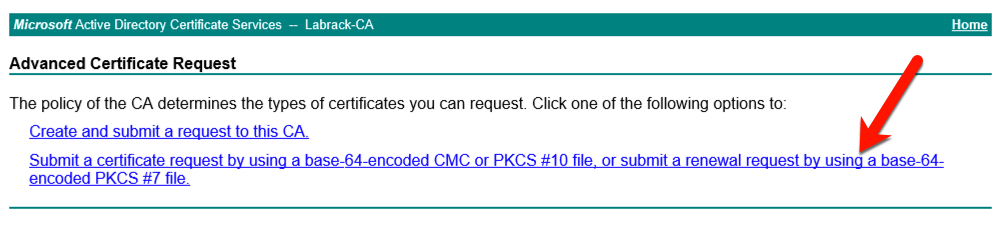
The last selection we need to make is the second link, the “Submit a certificate request by using a base-64-encoded or PKCS#10 file.”
When the form appears, paste in your CSR that we copied from the Windows Cert Utility. (or if you saved it to a file, open the file and copy and paste into the web form)
Then select “Web Server” as the Certificate Template type.
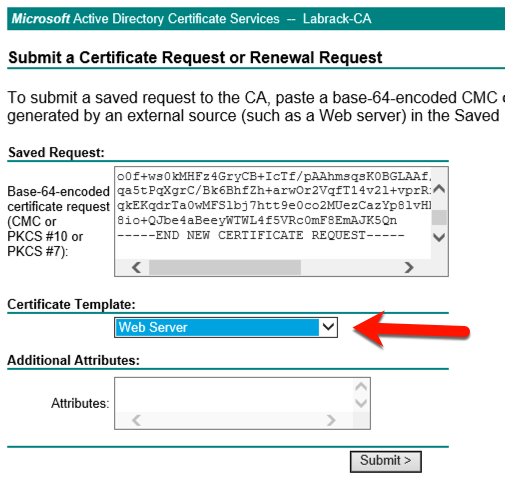
Press “Submit” to process the request.
The server should answer back by allowing you to download the new certificate files. The version that we want is the DER-encoded chain.
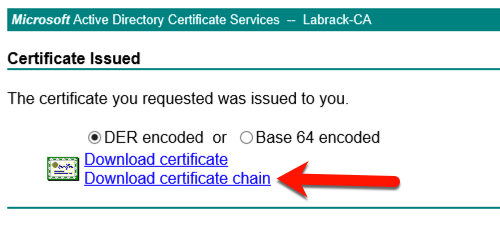
Save the file to your Documents folder, or somewhere else that you can remember on your ZVM. The file should have a p7b extension. As you can see I also downloaded the certificate on its own too, but this is not required.
Now that we have the Signed certificate we are done with the ADCS web page, and you can close your browser.
Importing the new certificate to the DigiCert Utility
Now we need to import our public key back into the DigiCert utility, this is because the utility keeps our private key safe and it will also convert the private and public keys into a single PFX file, which is what Zerto uses.
In the DigiCert Utility select the “Import” link, which is beside of the “Create CSR” link we used before.
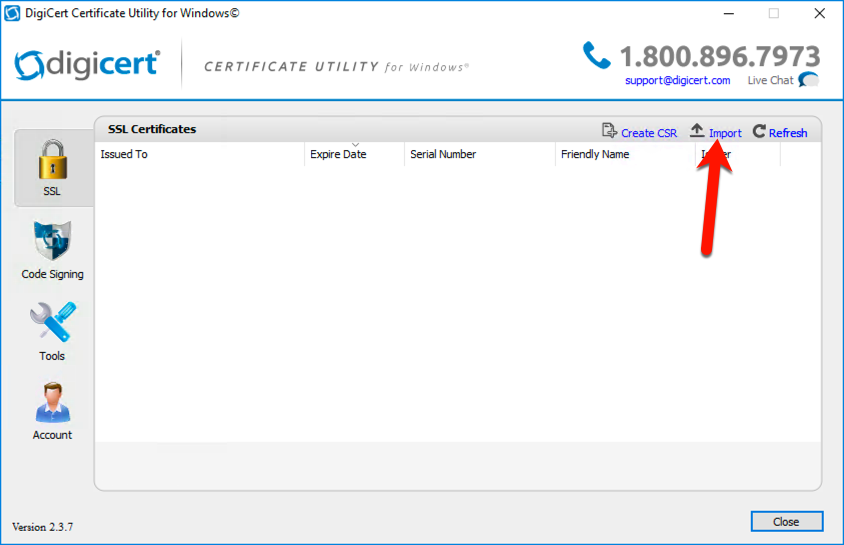
You will be asked where your public key is located. Select the file that you downloaded from the ADCS webpage, it is the one labeled as a PKCS#7 certificate and has the “.p7b” extension.
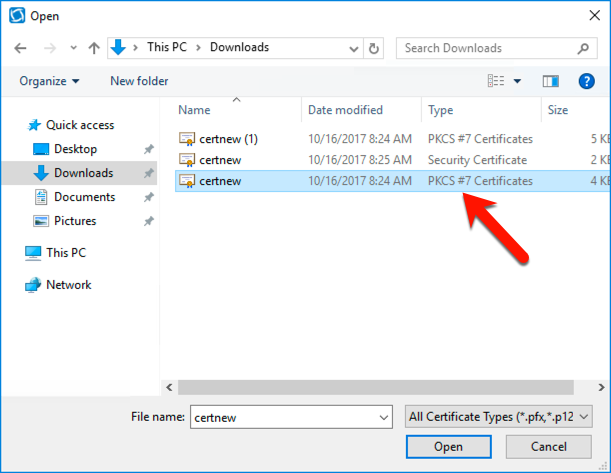
Click “Open”, next enter a name for your certificate. I’m pretty sure this is just for identification purposes.
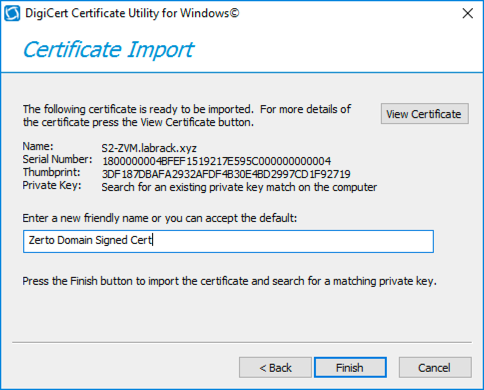
Then click “Finish.”
You should then see a box that says the key was successfully imported, and back on the SSL main page, you will see the certificate listed.
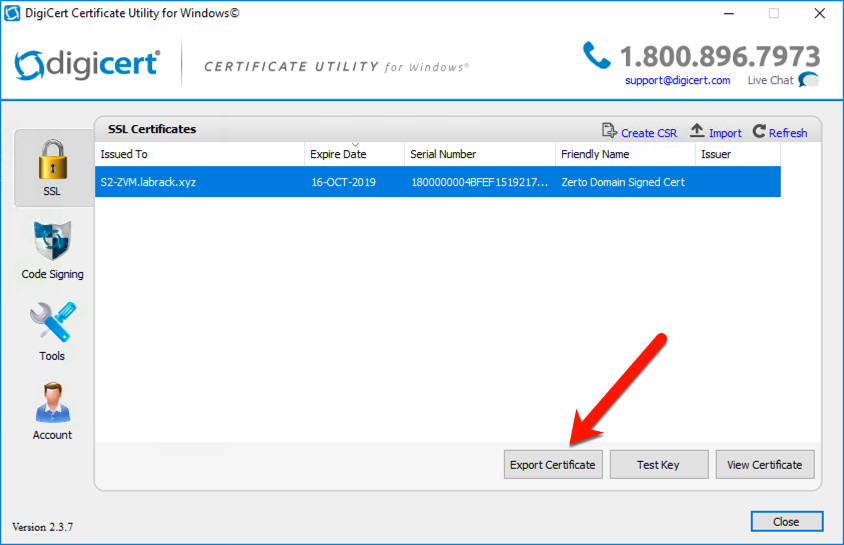
Exporting the PFX from DigiCert Utility
As I stated earlier, Zerto Virtual Manager expects the entire certificate chain to be in a PFX file, and that the file will be password protected. Luckily the DigiCert Utility makes the whole process easy.
There is an “Export Certificate” button at the bottom of the interface that we need to click to get started.

Next, select make sure the export options are the same as the screenshot below. The export settings should be:
“Yes, export the private key”
“pfs file” (make sure to check the “Include all certificates in the certificate path)
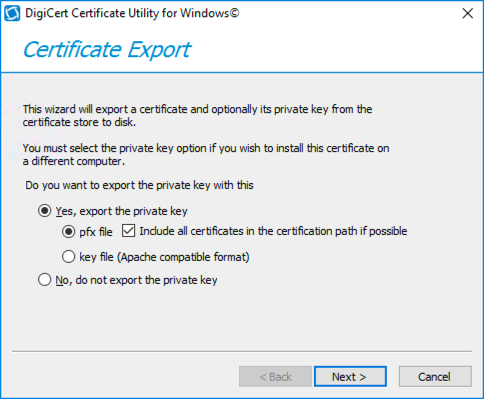
Then click “Next.”
You will need to enter a password to protect your PFX file. This is because this one file contains both the private and public key for your certificate.
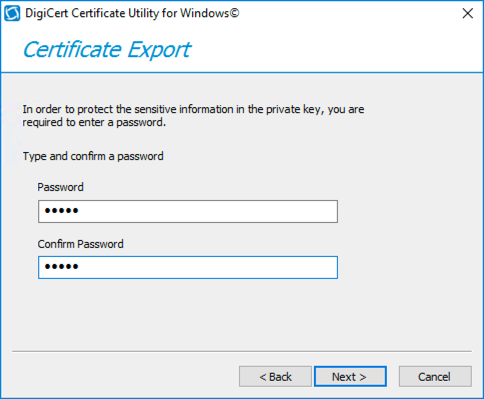
After entering a password, select a location to export the PFX file to. I would put it in your Documents folder or some other folder where you can find it.
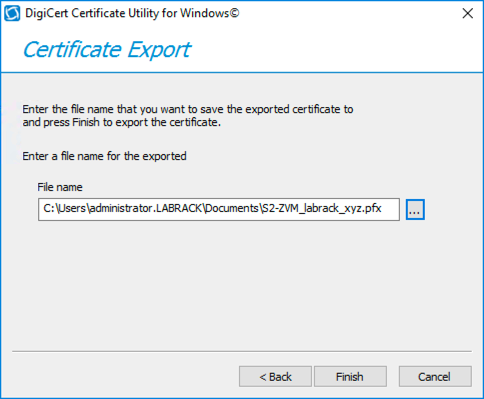
Click “Finish” to complete the export.
Importing the PFX into Zerto Virtual Manager
Now that we have a PFX file that is signed, we are ready to import it into ZVM. To get started launch the “Zerto Diagnostics” tool from the Start menu.
Then select “Reconfigure Zerto Virtual Manager”
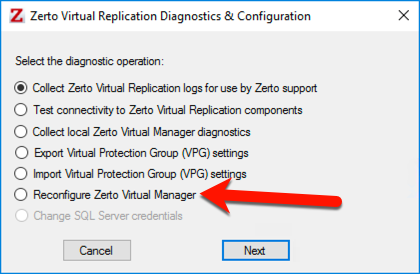
The only setting we need to change is on the third page of the config wizard, so you can safely skip through the pages until you come to this one.
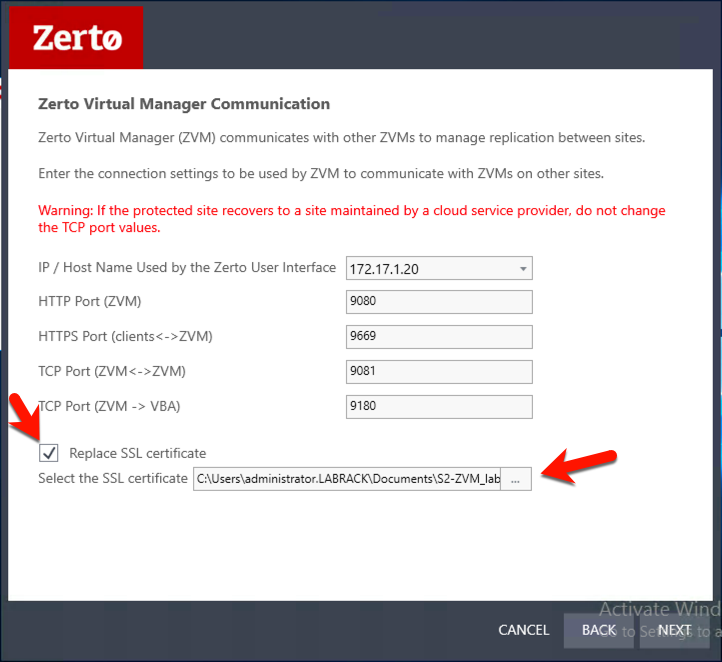
Click on the “Replace SSL certificate” box, and then select the PFX file that you saved in the last step.
You will be prompted for the PFX password that you set.
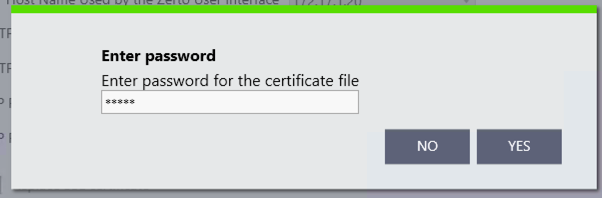
Click “Yes” once you have entered the password. Then proceed through the rest of the wizard, and click “Run” on the last page.
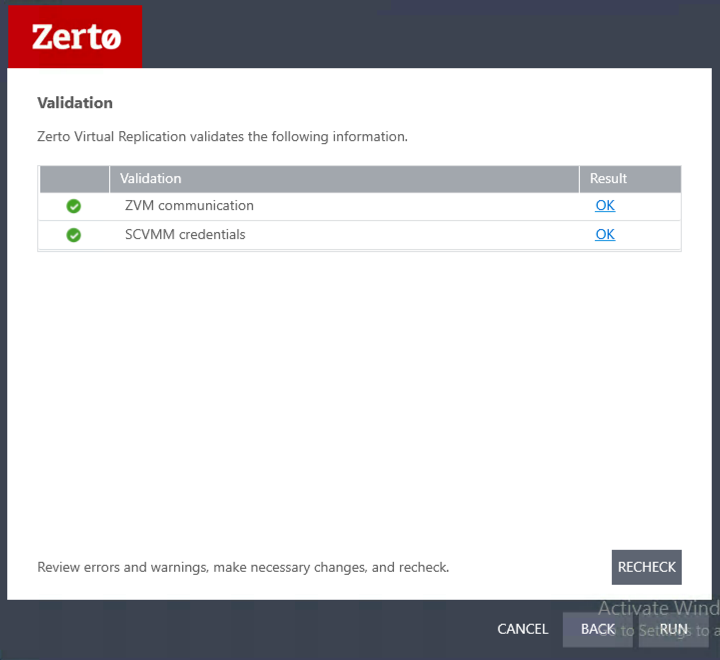
New Certificate Verification
The best place that I found to check for the new certificate is on Internet Explorer on a domain joined PC, as it will use the ADCS server by default.
If you click on the lock icon in the address bar you should see something like this:
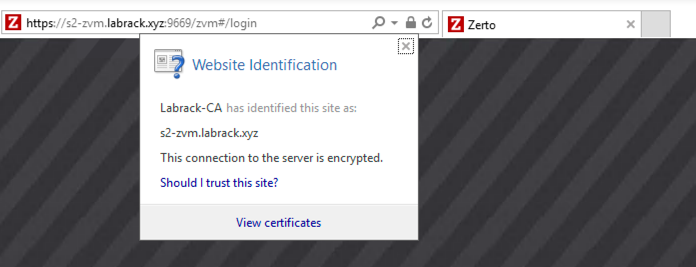
What we are looking for is the “Labrack-CA has identified this site as” … that means that our certificate is valid. Also, you shouldn’t get the “this site isn’t safe anymore” in Internet Explorer.
[stextbox id=’alert’]Note: If your PC isn’t joined to your domain, or hasn’t been configured with your ACCS server as an acceptable CA you will still get the SSL warning page.[/stextbox]
![]()





I completed this task a week or two ago, works for securing the browser communication. One issue I have, and appears you would have as well based on the screenshots, every time you open Vcenter console you receive the warning pop up that the communication is using the IP address but the certificate is signed with the name. You can click the box to import but that just makes the problem go away and doesn’t fix it. Based on my communication with Zerto support, you have unpair the sites so you can change the IP host name in the Zerto Reconfigure uitility, then pair back up and reimport your VPG Settings. Quite a painful process.